- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture

What is OSI Model? – Layers of OSI Model
The OSI (Open Systems Interconnection) Model is a set of rules that explains how different computer systems communicate over a network. OSI Model was developed by the International Organization for Standardization (ISO) . The OSI Model consists of 7 layers and each layer has specific functions and responsibilities.
This layered approach makes it easier for different devices and technologies to work together. OSI Model provides a clear structure for data transmission and managing network issues. The OSI Model is widely used as a reference to understand how network systems function.
In this article, we will discuss the OSI Model and each layer of the OSI Model in detail. We will also discuss the flow of data in the OSI Model and how the OSI Model is different from the TCP/IP Model.
Aiming for a top All India Rank in GATE CS & IT 2025 exam, but not sure where you stand? We’ve got you covered! Our GATE CS & IT Test Series – 2025 is designed to give you the edge you need. With previous year questions, subject-wise and full-length mock tests, and the All India mock Test, you can get a real feel of the exam. Plus, get our live mentorship classes with experts and attend live doubt-solving sessions to clear all your queries.
Layers of the OSI Model
There are 7 layers in the OSI Model and each layer has its specific role in handling data. All the layers are mentioned below:
Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
Application Layer
Layer 1 – Physical Layer
The lowest layer of the OSI reference model is the Physical Layer . It is responsible for the actual physical connection between the devices. The physical layer contains information in the form of bits. Physical Layer is responsible for transmitting individual bits from one node to the next. When receiving data, this layer will get the signal received and convert it into 0s and 1s and send them to the Data Link layer, which will put the frame back together. Common physical layer devices are Hub , Repeater , Modem , and Cables .

Functions of the Physical Layer
- Bit Synchronization: The physical layer provides the synchronization of the bits by providing a clock. This clock controls both sender and receiver thus providing synchronization at the bit level.
- Bit Rate Control: The Physical layer also defines the transmission rate i.e. the number of bits sent per second.
- Physical Topologies: Physical layer specifies how the different, devices/nodes are arranged in a network i.e. bus topology , star topology , or mesh topology .
- Transmission Mode: Physical layer also defines how the data flows between the two connected devices. The various transmission modes possible are Simplex, half-duplex and full-duplex .
Layer 2 – Data Link Layer (DLL)
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of the DLL to transmit it to the Host using its MAC address . Packet in the Data Link layer is referred to as Frame. Switches and Bridges are common Data Link Layer devices.
The Data Link Layer is divided into two sublayers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
The packet received from the Network layer is further divided into frames depending on the frame size of the NIC(Network Interface Card) . DLL also encapsulates Sender and Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.
Functions of the Data Link Layer
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit a set of bits that are meaningful to the receiver. This can be accomplished by attaching special bit patterns to the beginning and end of the frame.
- Physical Addressing: After creating frames, the Data link layer adds physical addresses ( MAC addresses ) of the sender and/or receiver in the header of each frame.
- Error Control: The data link layer provides the mechanism of error control in which it detects and retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both sides else the data may get corrupted thus, flow control coordinates the amount of data that can be sent before receiving an acknowledgment.
- Access Control: When a single communication channel is shared by multiple devices, the MAC sub-layer of the data link layer helps to determine which device has control over the channel at a given time.
Layer 3 – Network Layer
The network layer works for the transmission of data from one host to the other located in different networks. It also takes care of packet routing i.e. selection of the shortest path to transmit the packet, from the number of routes available. The sender and receiver’s IP address are placed in the header by the network layer. Segment in the Network layer is referred to as Packet. Network layer is implemented by networking devices such as routers and switches .
Functions of the Network Layer
- Routing: The network layer protocols determine which route is suitable from source to destination. This function of the network layer is known as routing.
- Logical Addressing: To identify each device inter-network uniquely, the network layer defines an addressing scheme. The sender and receiver’s IP addresses are placed in the header by the network layer. Such an address distinguishes each device uniquely and universally.
Layer 4 – Transport Layer
The transport layer provides services to the application layer and takes services from the network layer. The data in the transport layer is referred to as Segments . It is responsible for the end-to-end delivery of the complete message. The transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found. Protocols used in Transport Layer are TCP , UDP NetBIOS , PPTP .
At the sender’s side , the transport layer receives the formatted data from the upper layers, performs Segmentation , and also implements Flow and error control to ensure proper data transmission. It also adds Source and Destination port number in its header and forwards the segmented data to the Network Layer.
- Generally, this destination port number is configured, either by default or manually. For example, when a web application requests a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default ports assigned.
At the Receiver’s side, Transport Layer reads the port number from its header and forwards the Data which it has received to the respective application. It also performs sequencing and reassembling of the segmented data.
Functions of the Transport Layer
- Segmentation and Reassembly: This layer accepts the message from the (session) layer, and breaks the message into smaller units. Each of the segments produced has a header associated with it. The transport layer at the destination station reassembles the message.
- Service Point Addressing: To deliver the message to the correct process, the transport layer header includes a type of address called service point address or port address. Thus by specifying this address, the transport layer makes sure that the message is delivered to the correct process.
Services Provided by Transport Layer
- Connection-Oriented Service
- Connectionless Service
Layer 5 – Session Layer
Session Layer in the OSI Model is responsible for the establishment of connections, management of connections, terminations of sessions between two devices. It also provides authentication and security. Protocols used in the Session Layer are NetBIOS, PPTP.
Functions of the Session Layer
- Session Establishment, Maintenance, and Termination: The layer allows the two processes to establish, use, and terminate a connection.
- Synchronization: This layer allows a process to add checkpoints that are considered synchronization points in the data. These synchronization points help to identify the error so that the data is re-synchronized properly, and ends of the messages are not cut prematurely and data loss is avoided.
- Dialog Controller: The session layer allows two systems to start communication with each other in half-duplex or full-duplex.
Let us consider a scenario where a user wants to send a message through some Messenger application running in their browser. The “ Messenger ” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, optionally encrypted (if the data is sensitive), and converted into bits (0’s and 1’s) so that it can be transmitted.

Communication in Session Layer
Layer 6 – Presentation Layer
The presentation layer is also called the Translation layer . The data from the application layer is extracted here and manipulated as per the required format to transmit over the network. Protocols used in the Presentation Layer are JPEG , MPEG , GIF , TLS/SSL , etc.
Functions of the Presentation Layer
- Translation: For example, ASCII to EBCDIC .
- Encryption/ Decryption: Data encryption translates the data into another form or code. The encrypted data is known as the ciphertext and the decrypted data is known as plain text. A key value is used for encrypting as well as decrypting data.
- Compression: Reduces the number of bits that need to be transmitted on the network.
Layer 7 – Application Layer
At the very top of the OSI Reference Model stack of layers, we find the Application layer which is implemented by the network applications. These applications produce the data to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user. Protocols used in the Application layer are SMTP , FTP , DNS , etc.
Functions of the Application Layer
The main functions of the application layer are given below.
- Network Virtual Terminal(NVT): It allows a user to log on to a remote host.
- File Transfer Access and Management(FTAM): This application allows a user to access files in a remote host, retrieve files in a remote host, and manage or control files from a remote computer.
- Mail Services: Provide email service.
- Directory Services: This application provides distributed database sources and access for global information about various objects and services.
How Data Flows in the OSI Model ?
When we transfer information from one device to another, it travels through 7 layers of OSI model. First data travels down through 7 layers from the sender’s end and then climbs back 7 layers on the receiver’s end.
Data flows through the OSI model in a step-by-step process:
- Application Layer: Applications create the data.
- Presentation Layer: Data is formatted and encrypted.
- Session Layer: Connections are established and managed.
- Transport Layer: Data is broken into segments for reliable delivery.
- Network Layer : Segments are packaged into packets and routed.
- Data Link Layer: Packets are framed and sent to the next device.
- Physical Layer: Frames are converted into bits and transmitted physically.
Each layer adds specific information to ensure the data reaches its destination correctly, and these steps are reversed upon arrival.
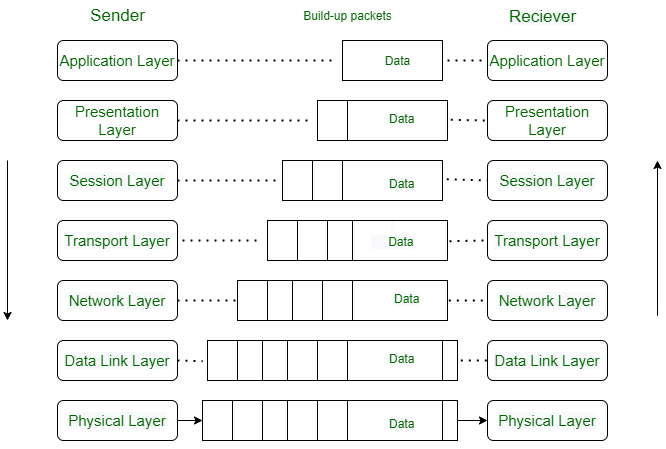
We can understand how data flows through OSI Model with the help of an example mentioned below.
Let us suppose, Person A sends an e-mail to his friend Person B .
Step 1: Person A interacts with e-mail application like Gmail , outlook , etc. Writes his email to send. (This happens at Application Layer ).
Step 2: At Presentation Layer, Mail application prepares for data transmission like encrypting data and formatting it for transmission.
Step 3: At Session Layer, There is a connection established between the sender and receiver on the internet.
Step 4: At Transport Layer , Email data is broken into smaller segments. It adds sequence number and error-checking information to maintain the reliability of the information.
Step 5: At Network Layer, Addressing of packets is done in order to find the best route for transfer.
Step 6: At Data Link Layer, d ata packets are encapsulated into frames, then MAC address is added for local devices and then it checks for error using error detection.
Step 7: At Physical Layer, Frames are transmitted in the form of electrical/ optical signals over a physical network medium like ethernet cable or WiFi.
After the email reaches the receiver i.e. Person B , the process will reverse and decrypt the e-mail content. At last, the email will be shown on Person B email client.
Protocols Used in the OSI Layers
Why does the osi model matter.
The OSI Model matters because it provides the user a clear structure of “how the data moves in the network?”. As the OSI Model consists of 7 layers, each layer has its specific role, and due to which it helps in understanding, identifying and solving the complex network problems easily by focusing on one of the layers not the entire network.
As the modern Internet does not prefer the OSI Model, but still, the OSI Model is still very helpful for solving network problems. It helps people understanding network concepts very easily.
Difference Between OSI and TCP/IP Model

OSI vs TCP/IP
Advantages of OSI Model
The OSI Model defines the communication of a computing system into 7 different layers. Its advantages include:
- It divides network communication into 7 layers which makes it easier to understand and troubleshoot.
- It standardizes network communications, as each layer has fixed functions and protocols.
- Diagnosing network problems is easier with the OSI model.
- It is easier to improve with advancements as each layer can get updates separately.
Disadvantages of OSI Model
- The OSI Model has seven layers, which can be complicated and hard to understand for beginners.
- In real-life networking, most systems use a simpler model called the Internet protocol suite (TCP/IP), so the OSI Model is not always directly applicable.
- Each layer in the OSI Model adds its own set of rules and operations, which can make the process more time-consuming and less efficient.
- The OSI Model is more of a theoretical framework, meaning it’s great for understanding concepts but not always practical for implementation.
In conclusion, the OSI (Open Systems Interconnection) model helps us understand how data moves in networks. It consists of seven distinct layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer has specific responsibilities and interacts with the layers directly above and below it. Since it is a conceptual model, but the OSI framework is still widely used to troubleshoot and understand networking issues.
Frequently Asked Questions on OSI Model – FAQs
Can osi layers work independently.
No, OSI layers do not work independently. Each layer depends on the services provided by the layer below it and, in turn, provides services to the layer above it. This layered approach ensures that data is transmitted smoothly from the source to the destination.
How does the OSI Model help in troubleshooting network issues?
By breaking down communication into layers, the OSI Model helps network administrators isolate problems more easily.
What happens if a layer in the OSI Model fails?
If a particular OSI layer fails, data transmission may be disrupted or fail entirely. Network administrator will check layer by layer to identify and resolve the issue, make sure that each layer is functioning correctly or not.
How does DNS fit into the OSI Model?
The Domain Name System (DNS) operates at Layer 7 (Application Layer). It translates domain names into IP addresses, facilitating communication between users and services across the network.
Similar Reads
- Computer Network Tutorial A computer network is a collection of computers or devices connected to share resources. Any device which can share or receive the data is called a Node. Through which the information or data propagate is known as channels, It can be guided or unguided. In this Computer network tutorial, you’ll lear 8 min read
Basics of Computer Network
- Basics of Computer Networking Computer networking is very important in modern technology, enabling the interconnected systems that power the Internet, business communications, and everyday digital interactions. Understanding the fundamentals of computer networking is essential for anyone involved in technology, from enthusiasts 14 min read
- Introduction to basic Networking Terminology For a specific purpose if things are connected together, are referred to as a NETWORK. A network can be of many types, like a telephone network, television network, computer network, or even a people network. Similarly, a COMPUTER NETWORK is also a kind of setup, where it connects two or more device 4 min read
- Goals of Networks Computer Network means an interconnection of autonomous (standalone) computers for information exchange. The connecting media could be a copper wire, optical fiber, microwave, or satellite. Networking Elements - The computer network includes the following networking elements: At least two computers 4 min read
- Basic Characteristics of Computer Networks Computer networks allow multiple devices to connect and share resources like files, printers, and internet access. Key characteristics include the network's size (like local or wide area), the way data is transferred (wired or wireless), and the network's layout (such as star or mesh). These feature 5 min read
- Challenges of Computer Network In the age of Internet where everyone loves to work with their computers and smart phones it is impossible to think any work without networking. With advancement of technology use of computer networking is increasing rapidly. In general if we will see, we can feel also how important networking is th 4 min read
- Physical Components of Computer Network The physical components of a computer network include hardware devices and media that enable connectivity and data exchange between devices. The server, client, peer, transmission media, and connecting devices make up the hardware components. A computer network is made up of several computers connec 6 min read
Network Hardware and Software
- Types of Computer Networks A computer network is a cluster of computers over a shared communication path that works to share resources from one computer to another, provided by or located on the network nodes. In this article, we will discuss computer networks and their types. What is a Computer Network?A computer network is 11 min read
- LAN Full Form A Local area network (LAN) is a network that is used to link devices in a single office, building, or campus of up to a short distance. LAN is restricted in size. In LAN networks internet speed is from 10 Mbps to 100 Mbps (But now much higher speeds can be achieved). The most common topologies used 10 min read
- How to Set Up a LAN Network? LAN (Local Area Network) is a data communication network that locally connects network devices such as workstations, servers, routers, etc. to share the resources within a small area such as a building or campus. Physical or wireless connections are set up between workstations to share the resources 4 min read
- MAN Full Form in Computer Networking A Metropolitan Area Network (MAN) is a type of computer network that spans over a metropolitan area, typically a city. It provides high-speed data communication services such as video, audio, and data transfer between multiple LANs (Local Area Networks) and WANs (Wide Area Networks). The main purpos 9 min read
- MAN Full Form MAN stands for Metropolitan Area Network and it is made by connecting multiple LANs. MAN covers a geographical area which is known as the metropolitan area. It serves as a connection that is larger than LAN(Local Area Network) but smaller than WAN(Wide Area Network). It generally covers the area of 5 min read
- WAN Full Form A WAN (Wide Area Network) is to connect multiple smaller Local Area Networks (LANs). It is a computer network designed. WANs can help in communication, the sharing of information, and much more between systems or devices from around the world through a WAN provider. What is a WAN?WAN stands for Wide 5 min read
- Introduction of Internetworking Internetworking is combined of 2 words, inter and networking which implies an association between totally different nodes or segments. This connection area unit is established through intercessor devices akin to routers or gateway. The first term for associate degree internetwork was catenet. This i 8 min read
- Difference between Internet, Intranet and Extranet Networks are crucial in today’s globalized world because they allow the acquisition, exchange, and organization of knowledge. Of all the first order networks the Internet, Intranet, and Extranet are commonly utilized for various applications. Every network type meets specific roles that are required 5 min read
- Protocol Hierarchies in Computer Network A Protocol Hierarchy is a fixed set of rules and conventions that govern the communication between two or more computers. The hierarchical structure allows for modular design, interoperability, and ease of implementation in computer networks. What is Protocol?A protocol is simply defined as a set of 3 min read
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter) Network devices are physical devices that allow hardware on a computer network to communicate and interact with each other. Network devices like hubs, repeaters, bridges, switches, routers, gateways, and brouters help manage and direct data flow in a network. They ensure efficient communication betw 10 min read
- Introduction of a Router Network devices are physical devices that allow hardware on a computer network to communicate and interact with one another. For example Repeater, Hub, Bridge, Switch, Routers, Gateway, Router, and NIC, etc. What is a Router?A Router is a networking device that forwards data packets between computer 12 min read
- Introduction of Gateways A gateway is a network connectivity device that connects two different configuration networks. Gateways are also known as protocol converters, because they play an important role in converting protocols supported by traffic on different networks. As a result, it allows smooth communication between t 5 min read
- What is a Network Switch and How Does it Work? The Switch is a network device that is used to segment the networks into different subnetworks called subnets or LAN segments. It is responsible for filtering and forwarding the packets between LAN segments based on MAC address. Switches have many ports, and when data arrives at any port, the desti 9 min read
Network Topology
- Types of Network Topology Network topology refers to the arrangement of different elements like nodes, links, or devices in a computer network. Common types of network topology include bus, star, ring, mesh, and tree topologies, each with its advantages and disadvantages. In this article, we will discuss different types of n 12 min read
- Difference between Physical and Logical Topology A Physical and Logical topologies are important concepts that govern the formation and operation of networks. In this article we will see differences between both topologies, and troubleshooting network infrastructure. What is Physical Topology?Physical topology indicates the arrangement of differen 5 min read
- What is OSI Model? - Layers of OSI Model The OSI (Open Systems Interconnection) Model is a set of rules that explains how different computer systems communicate over a network. OSI Model was developed by the International Organization for Standardization (ISO). The OSI Model consists of 7 layers and each layer has specific functions and re 14 min read
- Physical Layer in OSI Model The physical Layer is the bottom-most layer in the Open System Interconnection (OSI) Model which is a physical and electrical representation of the system. It consists of various network components such as power plugs, connectors, receivers, cable types, etc. The physical layer sends data bits from 5 min read
- Data Link Layer The data link layer is the second layer from the bottom in the OSI (Open System Interconnection) network architecture model. It is responsible for the node-to-node delivery of data. Its major role is to ensure error-free transmission of information. DLL is also responsible for encoding, decoding, an 5 min read
- Session Layer in OSI model Prerequisite : OSI Layer Introduction :The Session Layer is the 5th layer in the Open System Interconnection (OSI) model. This layer allows users on different machines to establish active communications sessions between them. It is responsible for establishing, maintaining, synchronizing, terminatin 5 min read
- Presentation Layer in OSI model Prerequisite : OSI Model Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extra 6 min read
- Application Layer in OSI Model The Application Layer of OSI (Open System Interconnection) model, is the top layer in this model and takes care of network communication. The application layer provides the functionality to send and receive data from users. It acts as the interface between the user and the application. The applicati 9 min read
- Protocol and Standard in Computer Networks Protocols and standards are important in computer networks. They are like the rules and guidelines that allow different devices and systems to communicate and work together smoothly. Protocols define how data is sent, received, and processed, while standards ensure that various technologies are comp 9 min read
- Examples of Data Link Layer Protocols Data Link Layer protocols are generally responsible to simply ensure and confirm that the bits and bytes that are received are identical to the bits and bytes being transferred. It is basically a set of specifications that are used for implementation of data link layer just above the physical layer 4 min read
TCP/IP Model
- TCP/IP Model The TCP/IP model is a fundamental framework for computer networking. It stands for Transmission Control Protocol/Internet Protocol, which are the core protocols of the Internet. This model defines how data is transmitted over networks, ensuring reliable communication between devices. It consists of 14 min read
- TCP/IP Ports and Its Applications A port is the logical address of any protocol; alternatively, we might think of a port as a special door for each protocol, through which all packets are routed. Another way to put it is that every protocol has a mailbox, or box, where every protocol packet is dropped. Subsequently, the recipient wi 6 min read
- What is TCP (Transmission Control Protocol)? TCP (Transmission Control Protocol) is one of the main protocols of the TCP/IP suite. It lies between the Application and Network Layers which are used in providing reliable delivery services. Transmission Control Protocol (TCP) ensures reliable and efficient data transmission over the internet. TCP 6 min read
- TCP 3-Way Handshake Process The TCP 3-Way Handshake is a fundamental process that establishes a reliable connection between two devices over a TCP/IP network. It involves three steps: SYN (Synchronize), SYN-ACK (Synchronize-Acknowledge), and ACK (Acknowledge). During the handshake, the client and server exchange initial sequen 7 min read
- Services and Segment structure in TCP The Transmission Control Protocol is the most common transport layer protocol. It works together with IP and provides a reliable transport service between processes using the network layer service provided by the IP protocol. The various services provided by the TCP to the application layer are as f 5 min read
- TCP Connection Establishment Prerequisite – TCP 3-Way Handshake Process TCP is a connection-oriented protocol and every connection-oriented protocol needs to establish a connection in order to reserve resources at both the communicating ends. Connection Establishment - TCP connection establishment involves a three-way handshake 3 min read
- TCP Connection Termination In TCP 3-way Handshake Process we studied that how connections are established between client and server in Transmission Control Protocol (TCP) using SYN bit segments. In this article, we will study how TCP close connection between Client and Server. Here we will also need to send bit segments to a 5 min read
- TCP Timers TCP uses several timers to ensure that excessive delays are not encountered during communications. Several of these timers are elegant, handling problems that are not immediately obvious at first analysis. Each of the timers used by TCP is examined in the following sections, which reveal its role in 4 min read
- Fast Recovery Technique For Loss Recovery in TCP When the RTO timer expires but an ACK is not received, the sender confirms that the packet is lost due to congestion at intermediary devices. Now sender has to tackle this congestion state carefully. Fast Recovery is the packet loss recovery technique. Recovery means becoming inactive and not transm 4 min read
- Difference Between OSI Model and TCP/IP Model Data communication is a process or act in which we can send or receive data. Understanding the fundamental structures of networking is crucial for anyone working with computer systems and communication. For data communication two models are available, the OSI (Open Systems Interconnection) Model, an 5 min read
Medium Access Control
- MAC Full Form MAC refers to Media Access Control, which is an important issue in network technology. In simple words, MAC is a series of rules through which devices can transfer data among them in a network. When a device is connected to a network, it obtains a unique MAC address. It identifies a device connected 5 min read
- Channel Allocation Problem in Computer Network Channel allocation is a process in which a single channel is divided and allotted to multiple users in order to carry user specific tasks. There are user's quantity may vary every time the process takes place. If there are N number of users and channel is divided into N equal-sized sub channels, Eac 3 min read
- Multiple Access Protocols in Computer Network Multiple Access Protocols are methods used in computer networks to control how data is transmitted when multiple devices are trying to communicate over the same network. These protocols ensure that data packets are sent and received efficiently, without collisions or interference. They help manage t 9 min read
- Carrier Sense Multiple Access (CSMA) Carrier Sense Multiple Access (CSMA) is a method used in computer networks to manage how devices share a communication channel to transfer the data between two devices. In this protocol, each device first sense the channel before sending the data. If the channel is busy, the device waits until it is 9 min read
- Collision Detection in CSMA/CD CSMA/CD (Carrier Sense Multiple Access/ Collision Detection) is a media access control method that was widely used in Early Ethernet technology/LANs when there used to be shared Bus Topology and each node ( Computers) was connected by Coaxial Cables. Nowadays Ethernet is Full Duplex and Topology is 7 min read
- Controlled Access Protocols in Computer Network Controlled Access Protocols (CAPs) in computer networks control how data packets are sent over a common communication medium. These protocols ensure that data is transmitted efficiently, without collisions, and with little interference from other data transmissions. In this article, we will discuss 6 min read
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ Stop and Wait ARQ is a Sliding Window Protocol method used for the reliable delivery of data frames. The stop-and-wait ARQ is used for noisy channels or links to handle flow and error control between sender and receiver. The Stop and Wait ARQ protocol sends a data frame and then waits for an acknowl 9 min read
- Sliding Window Protocol | Set 3 (Selective Repeat) Prerequisite : Sliding Window Protocol - Set 1 (Sender Side), Set 2 (Receiver Side) Why Selective Repeat Protocol? The go-back-n protocol works well if errors are less, but if the line is poor it wastes a lot of bandwidth on retransmitted frames. An alternative strategy, the selective repeat protoco 3 min read
- Piggybacking in Computer Networks Pre-Requisite: Transmission Mode in Computer Networks Piggybacking is the technique of delaying outgoing acknowledgment and attaching it to the next data packet. When a data frame arrives, the receiver waits and does not send the control frame (acknowledgment) back immediately. The receiver waits u 5 min read
IP Addressing
- What is IPv4? IP stands for Internet Protocol version v4 stands for Version Four (IPv4), is the most widely used system for identifying devices on a network. It uses a set of four numbers, separated by periods (like 192.168.0.1), to give each device a unique address. This address helps data find its way from one 4 min read
- What is IPv6? The most common version of the Internet Protocol currently is IPv6. The well-known IPv6 protocol is being used and deployed more often, especially in mobile phone markets. IP address determines who and where you are in the network of billions of digital devices that are connected to the Internet. It 5 min read
- Introduction of Classful IP Addressing An IP address is an address that has information about how to reach a specific host, especially outside the LAN. An IP address is a 32-bit unique address having an address space of 232. Classful IP addressing is a way of organizing and managing IP addresses, which are used to identify devices on a n 10 min read
- Classless Addressing in IP Addressing The Network address identifies a network on the internet. Using this, we can find a range of addresses in the network and total possible number of hosts in the network. Mask is a 32-bit binary number that gives the network address in the address block when AND operation is bitwise applied on the mas 7 min read
- Classful vs Classless Addressing Classful and Classless addressing are methods used in networking to manage IP addresses. Classful addressing divides IP addresses into fixed classes (A, B, C, D, E), each with predefined ranges. In contrast, classless addressing, also known as CIDR (Classless Inter-Domain Routing), offers more flexi 7 min read
- Classless Inter Domain Routing (CIDR) Classless Inter-Domain Routing (CIDR) is a method of IP address allocation and IP routing that allows for more efficient use of IP addresses. CIDR is based on the idea that IP addresses can be allocated and routed based on their network prefix rather than their class, which was the traditional way o 6 min read
- Supernetting in Network Layer Supernetting is the opposite of Subnetting. In subnetting, a single big network is divided into multiple smaller subnetworks. In Supernetting, multiple networks are combined into a bigger network termed a Supernetwork or Supernet. In this article, we'll explore the purpose and advantages of supernet 4 min read
- Introduction To Subnetting Subnetting is the process of dividing a large network into smaller networks called as "subnets." Subnets provides each group of devices have thier own space to communicate, that ultimately helps network to work easily. This also boosts security and makes it easier to manage the network, as each subn 8 min read
- Difference between Subnetting and Supernetting Subnetting is the procedure to divide the network into sub-networks or small networks, these smaller networks are known as subnets. The subnet is also defined as an internal address made up of a combination of a small network and host segments. In a subnet, a few bits from the host portion are used 4 min read
- Types of Routing Routing is the process of determining paths through a network for sending data packets. It ensures that data moves effectively from source to destination, making the best use of network resources and ensuring consistent communication. Routing performed by layer 3 (or network layer) devices to delive 6 min read
- Difference between Static and Dynamic Routing Routing is a vital communication mechanism that governs how data packets travel from source to destination. Effective routing ensures that data is transferred across networks in an efficient, reliable, and timely manner. There are two main forms of routing: static and dynamic. In this article, we wi 4 min read
- Unicast Routing - Link State Routing Prerequisite: Distance Vector Routing, Dijkstra algorithm Unicast means the transmission from a single sender to a single receiver. It is a point-to-point communication between the sender and receiver. There are various unicast protocols such as TCP, HTTP, etc. TCP is the most commonly used unicas 7 min read
- Distance Vector Routing (DVR) Protocol Distance Vector Routing (DVR) Protocol is a method used by routers to find the best path for data to travel across a network. Each router keeps a table that shows the shortest distance to every other router, based on the number of hops (or steps) needed to reach them. Routers share this information 5 min read
- Fixed and Flooding Routing algorithms In most situations, packets require multiple hops to make a journey towards the destination. Routing is one of the most complex and crucial aspects of packet-switched network design. Desirable Properties of Routing Algorithms:- Correctness and SimplicityRobustness: Ability of the network to deliver 5 min read
- Introduction of Firewall in Computer Network In the world of computer networks, a firewall acts like a security guard. Its job is to watch over the flow of information between your computer or network and the internet. It's designed to block unauthorized access while allowing safe data to pass through. Essentially, a firewall helps keep your d 12 min read
Congestion Control Algorithms
- Congestion Control in Computer Networks Congestion control is a crucial concept in computer networks. It refers to the methods used to prevent network overload and ensure smooth data flow. When too much data is sent through the network at once, it can cause delays and data loss. Congestion control techniques help manage the traffic, so al 8 min read
- Congestion Control techniques in Computer Networks Congestion control refers to the techniques used to control or prevent congestion. Congestion control techniques can be broadly classified into two categories: Open Loop Congestion ControlOpen loop congestion control policies are applied to prevent congestion before it happens. The congestion contro 5 min read
- Computer Network | Leaky bucket algorithm In the network layer, before the network can make Quality of service guarantees, it must know what traffic is being guaranteed. One of the main causes of congestion is that traffic is often bursty. To understand this concept first we have to know little about traffic shaping. Traffic Shaping is a m 11 min read
- TCP Congestion Control TCP congestion control is a method used by the TCP protocol to manage data flow over a network and prevent congestion. TCP uses a congestion window and congestion policy that avoids congestion. Previously, we assumed that only the receiver could dictate the sender’s window size. We ignored another e 4 min read
Network Switching
- Circuit Switching in Computer Network Circuit Switching is a type of switching, in which a connection is established between the source and destination before communication. This connection receives the complete bandwidth of the network until the data is transferred completely. However, circuit switching can be inefficient and costly du 9 min read
- Message switching techniques Switching is the technique by which nodes control or switch data to transmit it between specific points on a network. In message switching the entire message is transmitted without any break from one node to another. There is no direct link present between the sender and the receiver in message swit 4 min read
- Packet Switching and Delays in Computer Network Packet Switching in computer networks is a method of transferring data to a network in the form of packets. In order to transfer the file fast and efficiently over the network and minimize the transmission latency, the data is broken into small pieces of variable length, called Packet. At the destin 7 min read
- Differences Between Virtual Circuits and Datagram Networks Computer networks that provide connection-oriented services are called Virtual Circuits while those providing connection-less services are called Datagram networks. For prior knowledge, the Internet that we use is based on a Datagram network (connection-less) at the network level as all packets from 7 min read
Application Layer:DNS
- Domain Name System (DNS) in Application Layer The Domain Name System (DNS) is like the internet's phone book. It helps you find websites by translating easy-to-remember names (like www.example.com) into the numerical IP addresses (like 192.0.2.1) that computers use to locate each other on the internet. Without DNS, you would have to remember lo 10 min read
- Details on DNS DNS (Domain Name System) allows you to interact with devices on the Internet without having to remember long strings of numbers. Each computer on the Internet has its own unique address, known as an IP address, just like every home has a unique address for sending direct mail. 104.26.10.228 is an IP 5 min read
- Introduction to Electronic Mail Introduction:Electronic mail, commonly known as email, is a method of exchanging messages over the internet. Here are the basics of email:An email address: This is a unique identifier for each user, typically in the format of [email protected] email client: This is a software program used to send, 4 min read
- E-Mail Format Electronic Mail (e-mail) is one of the most widely used services of the Internet. This service allows an Internet user to send a message in a formatted manner (mail) to other Internet users in any part of the world. Message in the mail not only contain text, but it also contains images, audio and vi 3 min read
- World Wide Web (WWW) The World Wide Web (WWW), often called the Web, is a system of interconnected webpages and information that you can access using the Internet. It was created to help people share and find information easily, using links that connect different pages together. The Web allows us to browse websites, wat 6 min read
- HTTP Full Form HTTP stands for HyperText Transfer Protocol. It is the main way web browsers and servers communicate to share information on the internet. Tim Berner invents it. HyperText is the type of text that is specially coded with the help of some standard coding language called HyperText Markup Language (HTM 9 min read
- Streaming Stored Video Streaming of videos involve, storing of prerecorded videos on servers. Users send request to those servers.Users may watch the video from the start till the end, and may pause it anytime, do a forward or reverse skip, or stop the video whenever they want to do so. There are 3 video streaming categor 5 min read
- What is a Content Distribution Network and how does it work? Over the last few years, there has been a huge increase in the number of Internet users. YouTube alone has 2 Billion users worldwide, while Netflix has over 160 million users. Streaming content to such a wide demographic of users is no easy task. One can think that a straightforward approach to this 4 min read
CN Interview Quetions
- Top 50 Plus Networking Interview Questions and Answers for 2024 Networking is defined as connected devices that may exchange data or information and share resources. A computer network connects computers to exchange data via a communication media. Computer networking is the most often asked question at leading organizations such Cisco, Accenture, Uber, Airbnb, G 15+ min read
- Top 50 TCP/IP Interview Questions and Answers 2024 Understanding TCP/IP is essential for anyone working in IT or networking. It's a fundamental part of how the internet and most networks operate. Whether you're just starting or you're looking to move up in your career, knowing TCP/IP inside and out can really give you an edge. In this interview prep 15+ min read
- Top 50 IP Addressing Interview Questions and Answers In today’s digital age, every device connected to the internet relies on a unique identifier called an IP Address. If you’re aiming for a career in IT or networking, mastering the concept of IP addresses is crucial. In this engaging blog post, we’ll explore the most commonly asked IP address intervi 15+ min read
- Last Minute Notes - Computer Networks See Last Minute Notes on all subjects here. OSI Model Physical Layer Data Link layer Network Layer Transport Layer Presentation & Session layer Application Layer OSI ModelOSI stands for Open Systems Interconnection. It has been developed by ISO– International Organization for Standardization, in 11 min read
- Computer Network - Cheat Sheet A computer network is an interconnected computing device that can exchange data and share resources. These connected devices use a set of rules called communication protocols to transfer information over physical or wireless technology. Modern networks offer more than just connectivity. Enterprises 15+ min read
- Network Layer [mtouchquiz 103] 1 min read
- Transport Layer [mtouchquiz 104] 1 min read
- Application Layer [mtouchquiz 106] 1 min read
Improve your Coding Skills with Practice

What kind of Experience do you want to share?
The Cisco Learning Network
Osi model reference chart, aug 19, 2021 knowledge, information.
Those who start towards the path of CCNA understand the OSI model as a core component that continues throughout the rest of the Cisco certification tracks.
The Open Systems Interconnection model (OSI model) is a seven layer conceptual model that characterizes and standardizes the communication functions of a telecommunication or computing system.
The physical layer , which is the bottom layer of the OSI model, is concerned with the transmission and reception of the unstructured raw bit stream over a physical medium. It describes the electrical/optical, mechanical, and functional interfaces to the physical medium, and it carries the signals for all of the higher layers.
The data link layer provides error-free transfer of data frames from one node to another over the physical layer, allowing layers above it to assume virtually error-free transmission over the link.
The network layer controls the operation of the subnet, deciding which physical path the data should take based on network conditions, priority of service, and other factors.
The transport layer ensures that messages are delivered error-free, in sequence, and with no losses or duplications.
The session layer allows session establishment between processes running on different stations.
The presentation layer formats the data to be presented to the application layer. It can be viewed as the translator for the network. This layer may translate data from a format used by the application layer into a common format at the sending station, then translate the common format to a format known by the application layer at the receiving station.
The application layer serves as the window for users and application processes to access network services.
The Cisco Learning Network has developed an OSI model chart to help aid in your learning. This chart organizes and describes the seven layers, providing examples in the form of protocols and devices, as well as in relation to the DOD TCP/IP Model.

Article Details

Great summarized chart.

david.wadsworth80
Nice chart, though I would update it to include the TCP/IP 5 Layer model as well. For anyone looking at the OSI model, the top 3 layers (layer 7, 6, 5) are mapped to the Application layer for the TCP/IP model, with the lower layers (Layer 4 - Layer 1) are mapped 1:1, with the Data Link Layer mapped as the Network Interface Layer.

Thank you for sharing

Instant Like! Never thought that in here i could find so much Information for the self educated People.
Matt Saunders
Glad you like!

jdewitt2011
Very good information and definitely added value that we can download the OSI Model Chart for studying purposes. Even though the Transport layer is missing.
Thank you for sharing all this information with us.
You're welcome Nicole!
I appreciate you letting me know that the transport layer has now been added to the summary page.

akhilkamalakaran
A good one, thanks for share

This looks awesome!
Related Articles
- Number of Views 699
- Number of Views 4.98K
- Number of Views 20.55K
Trending Articles
- Cisco Packet Tracer: Software de Simulación para Redes
- 200-301 CCNA Study Materials
- Packet Tracer Labs
Communities: Recursos Educativos | |
Cisco.com © Copyright 2024 Cisco, Inc. All Rights Reserved. Privacy Statement Terms & Conditions Cookie Policy Trademarks
Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.
OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
Sase specific application service element, layer 7 application layer, layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.

- Trending Categories

- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
The Presentation Layer of OSI Model
The presentation layer (Layer 6) ensures that the message is presented to the upper layer in a standardized format. It deals with the syntax and the semantics of the messages.
The main functions of the presentation layer are as follows −
- It encodes the messages from the user dependent format to the common format and vice versa, for communication among dissimilar systems.
- It is responsible for data encryption and decryption of sensitive data before they are transmitted over common channels.
- It is also responsible for data compression. Data compression is done at the source to reduce the number of bits to be transmitted. It reduces the storage space and increases the file transfer rate. It is particularly useful for transmission of large multimedia files.
- Related Articles
- The Transport Layer of OSI Model
- The Session Layer of OSI Model
- The Data Link Layer of OSI Model
- Explain the functions of Presentation Layer.
- The OSI Reference Model
- What is Presentation Layer?
- What is a presentation layer?
- Advantages and Disadvantages of the OSI Model
- Computer Networks – Layers of OSI Model
- What is the OSI Reference Model?
- OSI Model in Computer Networking
- Why Does the OSI Reference Model Matter?
- What are the critiques of OSI Model and Protocols?
- Explain the advantages and disadvantages of the OSI reference Model
- OSI vs. TCP/IP Reference Model
Kickstart Your Career
Get certified by completing the course
COMPUTER NETWORK BASICS
- Introduction To Computer Networks
- Uses of Computer Networks
- Line Configuration
- Types of Network Topology
- Transmission Modes
- Transmission Mediums
- Bounded/Guided Transmission Media
- UnBounded/UnGuided Transmission Media
- Types of Communication Networks
- Connection Oriented and Connectionless Services
- Network Layer
- Quality of Service(QoS)
- IGMP Protocol
- Reference Models
Physical Layer
- Digital Transmission
- Multiplexing
- Circuit-Switched
- Message-Switched Networks
- Packet Switching
Data link layer
- Error Correction
- Data Link Control
- Flow and Error
- Simplest Protocol
- Stop-and-Wait Protocol
- Go-Back-N Automatic Repeat
- Sliding Window Protocol
- HDLC Protocol
- Point-to-Point Protocol
- Multiple Access in DL
- Channelization Protocols
- Gigabit Ethernet
- Random Access Protocol
- Controlled Access Protocols
- Carrier Sense Multiple Access
Transport layer
- Transport Layer
- Telnet vs SSH
- UDP Protocol
- TCP - Protocol
ISO/OSI REFERENCE MODEL
- Introduction to Reference Models
- OSI Model: Physical Layer
- OSI Model: Datalink Layer
- OSI Model: Network Layer
- OSI Model: Transport Layer
- OSI Model: Session Layer
- OSI Model: Presentation Layer
- OSI Model: Application Layer
TCP/IP REFERENCE MODELCOMPUTER NETWORKS
- The TCP/IP Reference Model
- Difference between OSI and TCP/IP Model
- Key Terms - Computer Network
Session layer
- Session Layer
Computer Networks
- Components of Computer Networks
- Features of Computer Network
- Protocols and Standards
- Connection Oriented and Connectionless
- OSI Vs TCP/IP
Presentation layer
- Presentation Layer
Application layer
- HTTP Protocol
- FTP Protocol
- SMTP Protocol
- POP Protocol
- SNMP Protocol
- Electronic Mail
- MIME Protocol
- World Wide Web
- DNS Protocol
Presentation Layer - OSI Reference Model
The primary goal of this layer is to take care of the syntax and semantics of the information exchanged between two communicating systems. Presentation layer takes care that the data is sent in such a way that the receiver will understand the information(data) and will be able to use the data. Languages(syntax) can be different of the two communicating systems. Under this condition presentation layer plays a role translator.
In order to make it possible for computers with different data representations to communicate, the data structures to be exchanged can be defined in an abstract way. The presentation layer manages these abstract data structures and allows higher-level data structures(eg: banking records), to be defined and exchanged.
Functions of Presentation Layer
- Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. The presentation layer is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats the network requires and the format the computer.
- Encryption: It carries out encryption at the transmitter and decryption at the receiver.
- Compression: It carries out data compression to reduce the bandwidth of the data to be transmitted. The primary role of Data compression is to reduce the number of bits to be 0transmitted. It is important in transmitting multimedia such as audio, video, text etc.
Design Issues with Presentation Layer
- To manage and maintain the Syntax and Semantics of the information transmitted.
- Encoding data in a standard agreed upon way. Eg: String, double, date, etc.
- Perform Standard Encoding on wire.
- ← Prev
- Next →
CN MCQ Tests
gate interview tests.

Sep 08, 2014
7.15k likes | 15.62k Views
OSI MODEL. Rahul Bandhe. Introduction.
Share Presentation
- network layer
- presentation layer
- network layer source
- session layer dialog initiation

Presentation Transcript
OSI MODEL Rahul Bandhe
Introduction • Open Systems Interconnection Basic Reference Model (OSI Reference Model or OSI Model) is an abstract description for layered communications and computer network protocol design. It was developed as part of the Open Systems Interconnection (OSI) initiative. In its most basic form, it divides network architecture into seven layers which, from top to bottom, are the Application, Presentation, Session, Transport, Network, Data-Link, and Physical Layers. It is therefore often referred to as the OSI Seven Layer Model.
OSI Model's 7 Layers APPLICATION Application to Application APPLICATION HIGHER LAYER Application to Application PRESENTATION PRESENTATION SESSION Application to Application SESSION TRANSPORT TRANSPORT Process to Process MIDDLE LAYER NETWORK NETWORK Source to Destination Router Source to Destination Hop to Hop DATA LINK DATA LINK Switch LOWER LAYER Hop to Hop Hub and Repeater PHYSICAL PHYSICAL Physical Medium
Host and Media Layer
Data, Protocol & Activities OSI Layers TCP/IP Suit Activities Application Application Telnet, FTP, SMTP, HTTP, DNS, SNMP, Specific address etc… To allow access to network resources Presentation Presentation To Translate, encrypt, and compress data Session Session To establish, manage, and terminate session Transport Transport SCTP, TCP, UDP, Sockets and Ports address To Provide reliable process-to-process Message delivery and error recovery Network Network IP, ARP/RARP, ICMP, IGMP, Logical address To move packets from source to destination; to provide internetworking Data Link Data Link IEEE 802 Standards, TR, FDDI, PPP, Physical address To organize bits into frames; to provide Hop-to-hop delivery Physical Physical Medium, Coax, Fiber, 10base, Wireless To Transmit bits over a medium; to provide Mechanical and electrical specifications
Physical Layer From data link layer To data link layer • One of the major function of the physical layer is to move data in the form of electromagnetic signals across a transmission medium. • Its responsible for movements of individual bits from one hop (Node) to next. • Both data and the signals can be either analog or digital. • Transmission media work by conducting energy along a physical path which can be wired or wireless • Concerned: • Physical characteristics of interface and medium (Transmission medium) • Representation of bits (stream of bits (0s or 1s) with no interpretation and encoded into signals) • Data rate (duration of a bit, which is how long it last) • Synchronization of bits (sender and receivers clock must be synchronized) • Line configuration (Point-to-Point, Point-to-Multipoint) • Physical topology • Transmission mode (Simplex, half duplex, full duplex) Physical layer Physical layer 110 10101000000010111 110 10101000000010111 Transmission medium
Data Link Layer (Host to Host) From network layer To network layer • Data link layer is responsible for moving frames from one hop (Node) to the next. • Concerned: • Framing (stream of bits into manageable data units) • Physical addressing (MAC Address) • Flow Control (mechanism for overwhelming the receiver) • Error Control (trailer, retransmission) • Access Control (defining master device in the same link) Data link layer Data link layer H2 Data T2 H2 Data T2 To physical layer From physical layer
Network Layer (Source to Destination) To transport layer From transport layer • The network layer is responsible for the delivery of individual packets from the source host to the destination host. • Concerned: • Logical addressing (IP Address) • Routing (Source to destination transmission between networks) Network layer Network layer H3 Data Packet H3 Data Packet To data link layer From data link layer
Transport Layer (Process to Process) From session layer From session layer • The transport layer is responsible for the delivery of a message from one process to another • Concerned: • Service-point addressing (Port address) • Segmentation and reassembly (Sequence number) • Connection control (Connectionless or connection oriented) • Flow control (end to end) • Error Control (Process to Process) Segments Segments Transport layer Transport layer H4 Data H4 Data H4 Data H4 Data H4 Data H4 Data To network layer From network layer
Session Layer (Dialog initiation) From Presentation layer To Presentation layer • The session layer is responsible for dialog control and synchronization • Concerned: • Dialog Control (Half Duplex/Full duplex) • Synchronization (Synchronization points, process inline within same page) H5 Data Data Data H5 Data Data Data Session layer Session layer Syn Syn Syn Syn Syn Syn To transport layer From transport layer
Presentation Layer (dependency) To application layer From application layer • The presentation layer is responsible for translation, compression and encryption • Concerned: • Translation (interoperability between different encoding system) • Encryption (Privacy schemes) • Compression (data compression) presentation layer H6 Data H6 Data presentation layer To session layer From session layer
Application Layer (user level service) USER (Human or Program) USER (Human or Program) • The application layer is responsible for providing services to the user. • Concerned: • Network virtual terminal (Software) • File transfer, access and management • Mail services • Directory services (access to distributed database sources for global information about various objects and services) X.500 FTAM X.400 X.500 FTAM X.400 Application layer Application layer H7 Data Message H7 Data Message To presentation layer From presentation layer
- More by User

OSI Model. Objectives. Describe the purpose of the OSI Model and each of its layers Explain specific functions belonging to each OSI Model layer Understand how two network nodes communicate through the OSI model Discuss the structure and purpose of data packets and frames
2.75k views • 31 slides

OSI Model. OSI MODEL. OSI Model. Communication Architecture. Strategy for connecting host computers and other communicating equipment. Defines necessary elements for data communication between devices. A communication architecture, therefore, defines a standard for the communicating hosts.
1.26k views • 18 slides
OSI Model. IP address. Type of Address. MAC address IP address. MAC to IP Address Comparison. MAC address Identifies a NIC in a computer on a network Each MAC address is unique
1.2k views • 26 slides
OSI MODEL. Introduction.
1.12k views • 12 slides

Computer Networks. OSI MODEL. OSI MODEL. The OSI model is a framework containing seven layers that defines the protocols and devices used at each stage of the process when data travels through a network
832 views • 14 slides

OSI Model. Guided by :- Mr . Alok kumar Jena. Presented by :- Rama Chandra Behera. Regd. No- 1005222009. CONTENTS OF OSI MODEL. What is OSI model ? Types of Layer . Explanation of each layer. Diagram Representation.
640 views • 14 slides

OSI Model. Topics to be discussed. Objective 7 Layers of OSI Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer. OBJECTIVE
619 views • 14 slides

OSI model. Content analysis. Meshal 202322421 Faisal 202322420. 1-What is OSI ?. The Open Systems Interconnection Basic Reference Model (OSI Model) is an abstract description for network protocol design, developed as an effort to standardize networking.
2.1k views • 20 slides

OSI Model. Open Systems Interconnection (OSI) is a set of internationally recognized, non-proprietary standards for networking and for operating system involved in networking functions. 7 Layers 7. Application Layer 6. Presentation Layer 5. Session Layer 4. Transport Layer
715 views • 25 slides

OSI Model. CS363-Winter 1999 DePaul University. Group Project Info. Teams formed and on the web Cases Working in Groups Last half of class tonight reserved for projects. Review #1.
510 views • 30 slides

OSI Model. MIS 416 – Module II Spring 2002 Networking and Computer Security. Topics. The OSI reference model Services in the OSI model. OSI Reference Model. OSI Reference Model - internationally standardised network architecture.
619 views • 17 slides

OSI Model. The OSI Model. Open Systems Interconnection Standard Model for Data Communications Specified by International Standards Organization (ISO) Adopted by CCITT/ITU Official Model Explained in X.200 Series. The OSI Model. Layered Approach to Communications Seven Layers Altogether
683 views • 12 slides

OSI Model. OSI MODEL. Presented by Aditya Kumar Gupta Lecturer, Department of Computer Application SMS Varanasi. OSI Model. Communication Architecture. Strategy for connecting host computers and other communicating equipment.
629 views • 18 slides

OSI Model. Open Systems Interconnection (OSI) is a set of internationally recognized, non-proprietary standards for networking and for operating system involved in networking functions. 7 Layers. A ll P eople S eem T o N eed D ata P rocessing. 7 . Application Layer
532 views • 20 slides
Strategy for connecting host computers and other communicating equipment.Defines necessary elements for data communication between devices. for more info:-http://bit.ly/1rOCOXB
327 views • 18 slides

394 views • 12 slides

OSI Model. OSI Reference Model By Vibhav Krashan Chaurasiya. Topics. The OSI reference model Services in the OSI model. OSI Reference Model. OSI Reference Model - internationally standardised network architecture.
676 views • 17 slides
OSI Seven Layers Model Explained with Examples
This tutorial explains the OSI reference model. Learn the seven layers of the OSI model and the functions of each layer in detail through examples.
The OSI (Open System Interconnection) reference model is a comprehensive set of standards and rules for hardware manufacturers and software developers. By following these standards, they can build networking components and software applications that work in any environment. It was published in 1984 by ISO (International Organization for Standardization).
It provides a framework for creating and implementing networking standards, devices, and internetworking schemes. It explains the networking from a modular perspective, making it easier to understand and troubleshoot.
Seven layers of the OSI Model
The OSI model has seven different layers, which are divided into two groups. The following table lists all the layers with their names and numbers.

Let’s understand each layer in detail.
This tutorial is the second part of the article " Networking reference models explained in detail with examples. ". Other parts of this article are the following.
This tutorial is the first part of the article. It summarizes why the OSI model was created and what advantages it has.
This tutorial is the third part of the article. It compares the OSI reference model with the TCP/IP model and lists the similarities and differences between both.
This tutorial is the fourth part of the article. It explains the five layers of the TCP/IP model in detail.
This tutorial is the fifth part of the article. It explains how data is encapsulated and de-encapsulated when it passes through the layers.
The Application Layer
This is the last and topmost layer of the OSI model. This layer provides an interface between the local system and the application program running on the network. If an application wants to use the resources available on the remote system, it interacts with this layer. Then, this layer provides the protocols and services that the application needs to access those resources.
There are two types of application programs: Network-aware and Network-unaware . An application program is considered a Network-aware application if it can make any type of network request. If an application program cannot make any type of network request, it is considered a Network-unaware program.
Network-aware programs are further divided into two types.
Programs that are mainly built to work on a local system. This type of program occasionally accesses the network for particular reasons such as updates, documentation, and troubleshooting. MS-Word, Adobe-Photoshop, and VLC Player are examples of this type of program.
Programs that are mainly built to work with a remote system. This type of program provides a platform to access resources available on a remote system. This type of program only works if the system is connected to the network. SSH, FTP, and TFTP are examples of this type of program.
The Application layer describes only the programs which fall in the second type. But it doesn’t mean that the first type of programs can’t take the advantage of the Application layer. It simply means that they are not documented in the Application layer. But if required, they can also connect to the network through the Application layer.
The Top layer of the OSI model is the application layer. It provides the protocols and services that are required by the network-aware applications to connect to the network. FTP, TFTP, POP3, SMTP, and HTTP are examples of standards and protocols used in this layer.
The Presentation Layer
The sixth layer of the OSI model is the Presentation layer. Applications running on the local system may or may not understand the format that is used to transmit the data over the network. The presentation layer works as a translator. When receiving data from the Application layer, it converts that data in such a format that can be sent over the network. When receiving data from the Session layer, it reconverts the data in such a format that the application, which will use it, can understand.
Conversion, compression, and encryption are the main functions that the Presentation layer performs on the sending computer while on the receiving computer these functions are reconversion, decompression, and decryption. ASCII, BMP, GIF, JPEG, WAV, AVI, and MPEG are examples of standards and protocols that work in this layer.
The Session Layer
The session layer is the fifth layer of the OSI model. It is responsible for setting up, managing, and dismantling sessions between presentation layer entities and providing dialogs between computers.
When an application makes a network request, this layer checks whether the requested resource is available on the local system or on a remote system. If the requested resource is available on a remote system, it tests whether a network connection to access that resource is available or not. If a network connection is not available, it sends an error message back to the application informing that the connection is not available.
If a network connection is available, it establishes a session with the remote system. For each request, it uses a separate session. This allows multiple applications to send or receive data simultaneously. When data transmission is completed, it terminates the session.
The session layer is responsible for establishing, managing, and terminating communications between two computers. RPCs and NFS are examples of the session layer.
The Transport Layer
The transport layer is the fourth layer of the OSI model. It provides the following functionalities: -
Segmentation
On the sending computer, it breaks the data stream into smaller pieces. Each piece is known as a segment and the process of breaking the data stream into smaller pieces is known as the segmentation . On the receiving computer, it joins all segments to recreate the original data stream.
Data transportation
This layer establishes a logical connection between the sending system and receiving system and uses that connection to provide end-to-end data transportation. This process uses two protocols: TCP and UDP.
The TCP protocol is used for reliable data transportation. TCP is a connection-oriented protocol. UDP protocol is used for unreliable data transportation. UDP is a connection-less protocol.
The main difference between a connection-less and connection-oriented protocol is that a connection-oriented protocol provides reliable data delivery. For reliable data delivery, it uses several mechanisms such as the three-way handshake process, acknowledgments, sequencing, and flow control.
Multiplexing
Through the use of port numbers, this layer also provides connection multiplexing. Connection multiplexing allows multiple applications to send and receive data simultaneously.
The main functionalities of the Transport layer are segmentation, data transportation, and connection multiplexing. For data transportation, it uses TCP and UDP protocols. TCP is a connection-oriented protocol. It provides reliable data delivery.
The Network Layer
The third layer of the OSI model is the Network Layer. This layer takes the data segment from the Transport layer and adds a logical address to it. A logical address has two components; network partition and host partition. The Network partition is used to group networking components while the host partition is used to uniquely identify a system on the network. A logical address is known as the IP address. Once the logical address and other related information are added to the segment , it becomes the packet .
This layer decides whether the packet is intended for the local system or a remote system. It also specifies the standards and protocols which are used to move data packets over networks.
To move data packets between two different networks, a device known as the router is used. Routers use the logical address to make the routing decision. Routing is the process of forwarding data packets to their destination.
Defining logical addresses and finding the best path to reach the destination address are the main functions of this layer. Routers work in this layer. Routing also takes place in this layer. IP, IPX, and AppleTalk are examples of this layer.
The Data Link Layer
The Data Link Layer is the second layer of the OSI model. This layer defines how networking components access the media and what transmission methods they use. This layer has two sub-layers: MAC and LLC.
MAC (Media Access Control)
This sub-layer defines how the data packets are placed in media. It also provides physical addressing. The physical address is known as the MAC address. Unlike logical addresses that need to be configured, physical addresses are pre-configured in NIC. The MAC address is used to uniquely identify a host in the local network.
LLC (Logical Link Control)
This sub-layer identifies the network layer protocol. On the sending computer, it encapsulates the information of the Network Layer protocol in the LLC header from which the Data Link layer receives the data packet. On the receiving computer, it checks the LLC header to get the information about the network layer protocol. This way, a data packet is always delivered to the same network layer protocol from which it was sent.
Defining physical addresses, finding hosts in the local network, specifying standards and methods to access the media are the primary functions of this layer. Switching takes place in this layer. Switches and Bridges work in this layer. HDLC, PPP, and Frame Relay are examples of this layer.
The Physical Layer
The Physical Layer is the first layer of the OSI model. This layer specifies the standards for devices, media, and technologies that are used in moving the data across the network such as:-
- Type of cable used in connecting the devices
- Patterns of pins used in both sides of the cable
- Type of interface-card used in the networking device
- Type of connector used to connect the cable with the network interface
- Encoding of digital signals received from the Data Link layer based on the attached media type such as electrical for copper, light for fiber, or a radio wave for wireless.
On the sending computer, it converts digital signals received from the Data Link layer, into analog signals and loads them on the physical media. On the receiving computer, it picks analog signals from the media and converts them into digital signals, and transfers them to the Data Link layer for further processing.
The Physical Layer mainly defines standards for media and devices that are used to move data across the network. 10BaseT, 10Base100, CSU/DSU, DCE, and DTE are examples of the standards used in this layer.
That’s all for this tutorial. In the next part of this article, we will compare the OSI model with the TCP/IP model and explains the similarities and differences between both models. If you like this tutorial, please don’t forget to share it with friends.
By ComputerNetworkingNotes Updated on 2024-10-16
ComputerNetworkingNotes CCNA Study Guide OSI Seven Layers Model Explained with Examples
- EtherChannel Load Distribution Explained
- Link Aggregation Control Protocol (LACP) Explained
- Port Aggregation Protocol (PAgP) Explained
- EtherChannel Manual Configuration
- EtherChannel Basic Concepts Explained
- STP, RSTP, PVST, RPVST, and MSTP
- Similarities and Differences between STP and RSTP
- RSTP / RPVST Explained with Examples
- PVST/RPVST and EtherChannel Explained
- STP/RSTP Timers Explained
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

IMAGES
VIDEO
COMMENTS
Prerequisite : OSI Model Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network.
Study with Quizlet and memorize flashcards containing terms like Which of the following are layers of the OSI reference model? (Select three.) Encryption Layer •WAN Layer •Presentation Layer •Transmission Layer •Application Layer •Session Layer •Connection Layer, What is a Protocol Data Unit (PDU)? •A type of encryption used in data transmission •A chunk of data with protocol ...
The lowest layer of the OSI reference model is the Physical Layer. It is responsible for the actual physical connection between the devices. ... Prerequisite : OSI Model Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data ...
The presentation layer formats the data to be presented to the application layer. It can be viewed as the translator for the network. ... osi-model-reference-chart. Summary. ... For anyone looking at the OSI model, the top 3 layers (layer 7, 6, 5) are mapped to the Application layer for the TCP/IP model, with the lower layers (Layer 4 - Layer 1 ...
In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the ...
The Presentation Layer of OSI Model - The presentation layer (Layer 6) ensures that the message is presented to the upper layer in a standardized format. It deals with the syntax and the semantics of the messages.The main functions of the presentation layer are as follows −It encodes the messages from the user dependent format to the
OSI Model. OSI stands for Open System Interconnection is a reference model that describes how information from a software application in one computer moves through a physical medium to the software application in another computer.; OSI consists of seven layers, and each layer performs a particular network function. OSI model was developed by the International Organization for Standardization ...
The presentation layer manages these abstract data structures and allows higher-level data structures(eg: banking records), to be defined and exchanged. Functions of Presentation Layer Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams.
OSI MODEL Rahul Bandhe. Introduction • Open Systems Interconnection Basic Reference Model (OSI Reference Model or OSI Model) is an abstract description for layered communications and computer network protocol design. It was developed as part of the Open Systems Interconnection (OSI) initiative. In its most basic form, it divides network architecture into seven layers which, from top to ...
It compares the OSI reference model with the TCP/IP model and lists the similarities and differences between both. TCP/IP Reference Model Explained . This tutorial is the fourth part of the article. It explains the five layers of the TCP/IP model in detail. ... The sixth layer of the OSI model is the Presentation layer. Applications running on ...